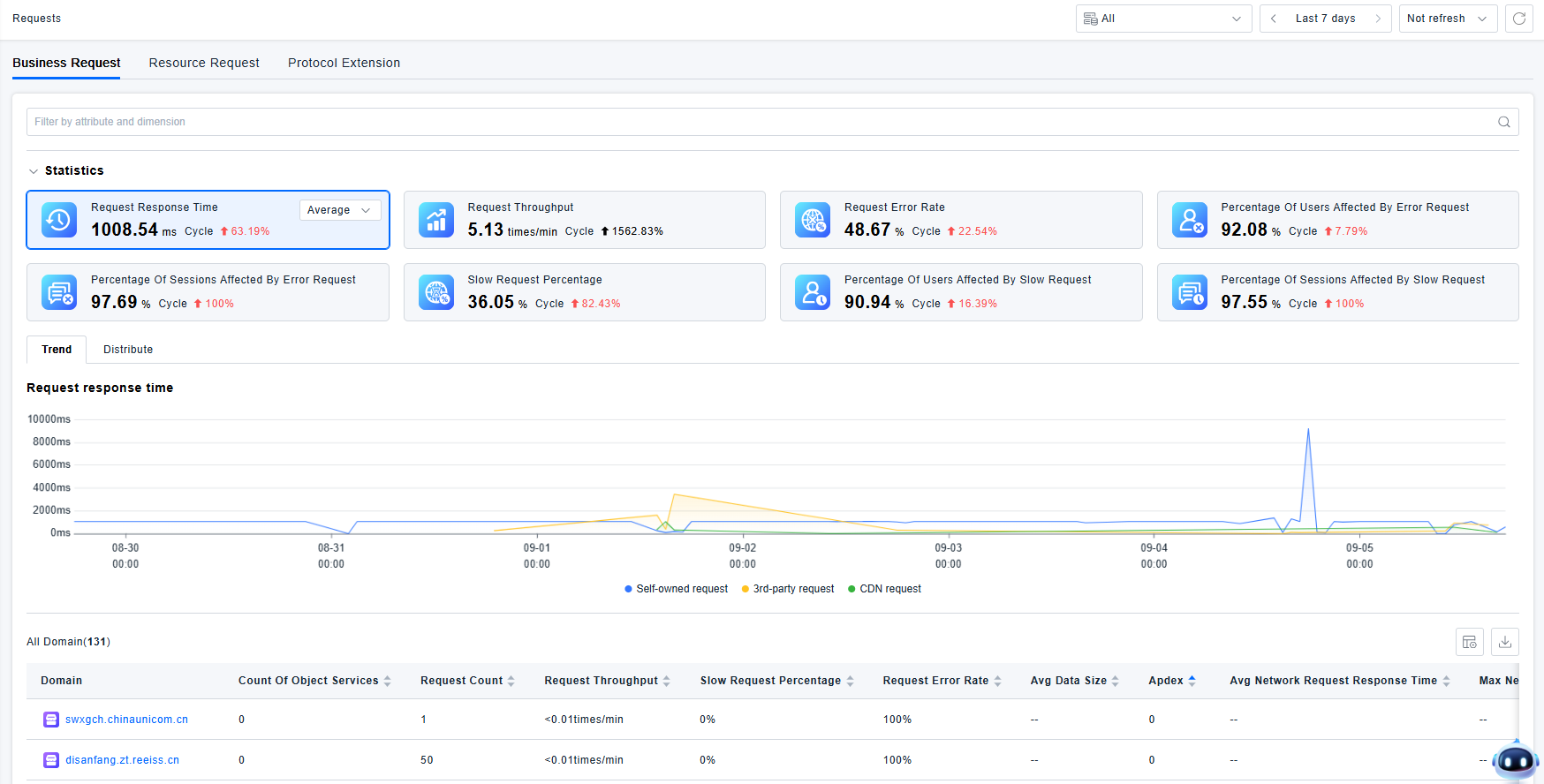
Requests
In Real User Monitoring (RUM), network requests are a core analysis object. They connect three critical links: "user experience perception," "frontend interaction response," and "backend service capability." Network requests serve as the most direct data carrier for pinpointing the root causes of "user experience lag/operation failure," quantifying "system service quality," and correlating "business operation success or failure." They are also the essential bridge from "surface-level experience issues" to "underlying technical bottlenecks."
To view detailed request analysis data, navigate to Rqquests Analysis.
Definition
A network request refers to the process where a client (e.g., browser, mobile app, mini-program) sends a data request to a server or other network node and expects to receive response data. It is the core technical behavior enabling cross-device, cross-network data interaction and the foundation for internet applications to achieve "dynamic data loading, functional interaction, and state synchronization."
Example: When a client (e.g., app, web page) actually sends a POST request containing account credentials to the target address (e.g., https://api.example.com/user/login) according to the API specification and waits for the server to return a result, this dynamic "send → receive" process constitutes a network request.
Network Request Types
| Type | Description |
|---|---|
| Resource Request | Requests for resources such as images, audio/video, text, etc. |
| Protocol Extension | Network requests using protocols other than HTTP. |
| Business Request | All network requests that are not Resource Requests or Protocol Extensions. |
Identification Rules
Functional Scenario
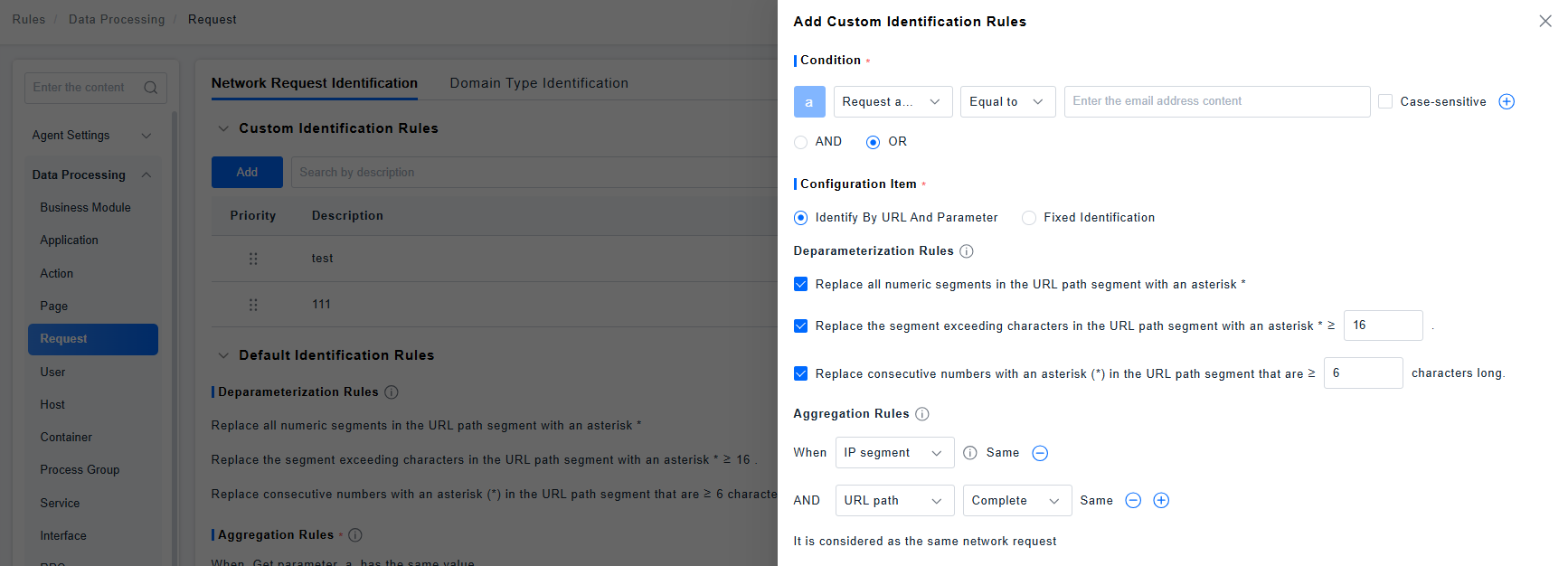
Different applications have varied implementation logic. It's necessary to combine actual scenarios and flexibly define network request identification rules using domains, IP segments, URL paths, Header parameters, GET parameters, and POST parameters. This ensures precise determination of which instances should be considered the same network request, aligning with business needs for aggregated network request analysis.
For the collected raw URL, parameter stripping rules are executed first to avoid interference from irrelevant parameters. Aggregation rules are then applied to group requests based on core characteristics. Through these two steps, requests that are essentially the same network request but have different URLs can be aggregated into one, ensuring the accuracy and consistency of network request analysis.
Getting Started
Aggregation Rules
Supports aggregation based on the domain, IP segment, URL path, URL parameters, Header parameters,and Body parameters of a network request.
For example, if you set the page identification rule to: URLs with identical paths are considered the same network request, the identification logic would be as follows:
Parameter Stripping Rules
To avoid interference from IDs and other dynamic values within the URL path during identification, specific parameter stripping rules are supported. You can configure these rules as needed by selecting the appropriate stripping rule and specifying the length parameters to be stripped.
